SUSCTF2022
简述:应该是第一次和syclover的师傅们一块参与到比赛中(tql就出一道签到,不算),本次做出了4道题,两道逆向,两道misc,只交了两道misc,逆向师傅太强了!!!

师傅们都太强了!!!!!
re
DigitalCircuits
给了一个exe的包,包上图片是python。在极客大挑战中就遇到过这种问题,我们首先将exe转成pyc文件:
1 | python pyinstxtractor.py DigitalCircuits.exe |
然后取出生成文件夹的struct和同名pyc文件,将struct文件前16字节覆盖到pyc文件上,然后反编译pyc文件。
1 | uncompyle6 DigitalCircuits.pyc > DigitalCircuits.py |
得到源码:
1 | import time |
很显然从f10能看出这就是个tea加密,并且没有魔改:
但从res能看出是3组数组,不是4组,所以给出脚本:
1 |
|
解出来,转换成字符串,然后套上壳。
hell_world
这个题听师傅说与西湖论剑的题是一样的。怪不得出那么快,我们来好好看一下这个题,有点像hgame里面那道虚拟机的题
这个题运行顺序是:0 – 1 – 2 – 3,在3出进行一次字符串判断,长度是44才能到4去,如果不是到5,然后输出wrong。
看内存发现输入数据存入了a1数组

然后转到9 – 10 – 11
其中case9是将输入转化为二进制,只是0和1使用2和3来替换,接着执行的case10是使用异或数组与输入进行异或操作且转化为二进制。
1 | case 9: |
我们看到case11处,我们能动调出比较函数,那么一定存在加密后的值,v71–》v6,所以找到了密文,我们输入经过加密就跟密文对比。

那么我们很容易就写出脚本了:
1 | data1 = [86, |
K.O
tttree
刚看的时候感觉是个二叉树,但无法反汇编,所以只能审代码。有点难度,复现一下:
misc
本次misc出了很快,这种感觉很不错,但我很烦题目都是英文,翻译根本翻不了。。。
ra2
红警游戏,让找旗子,说什么降落到了月球,设定是晚上很危险,白天安全,那直接把白天时间拉满不就行了。
找到目录\Romanovs-Vengeance\mods\rv\maps\ctf-01,找到ctf-01.lua文件,改几个数据

把时间无限延长,然后进去放几个狗,乱跑找flag

这个体验不错,就我在图书馆玩游戏,笑死。。
Tanner
这个题其实我第一天就有思路,而且差不多出来了,就是他这个英文翻译很不准确。。真服了,导致我虚拟机没写完呢,今天还要赶虚拟机。。

这个图,应该是lpdc的另一种表示,可以表示成矩阵,checknodes当成行,bitnodes当成列,得到(10,5)矩阵,题目给了这样一段提示
1 | THE FLAG IS the sha256 of the sum ofthe proper codewords(binary plus)which satisfy the condition.(note: with no zeros front) |
我纯纯文盲,应该是让求码字,note的意思应该是最后sum的和前面不能加0,而不是不能用码字求和。。。。
1 | import numpy as np |
得到许多二进制,我们求和
1 | a = |
求得的值再sha256,用小写形式交了!!大写不行!!!
audio
如果给出了原音频和加密过的音频,要进行音频相消!
把两段音频同时拖进audacity里面,然后分别对音频进行标准化,然后分别截去静音,然后对fromfriends.wav进行反相操作,而后把两段音频叠起来即可
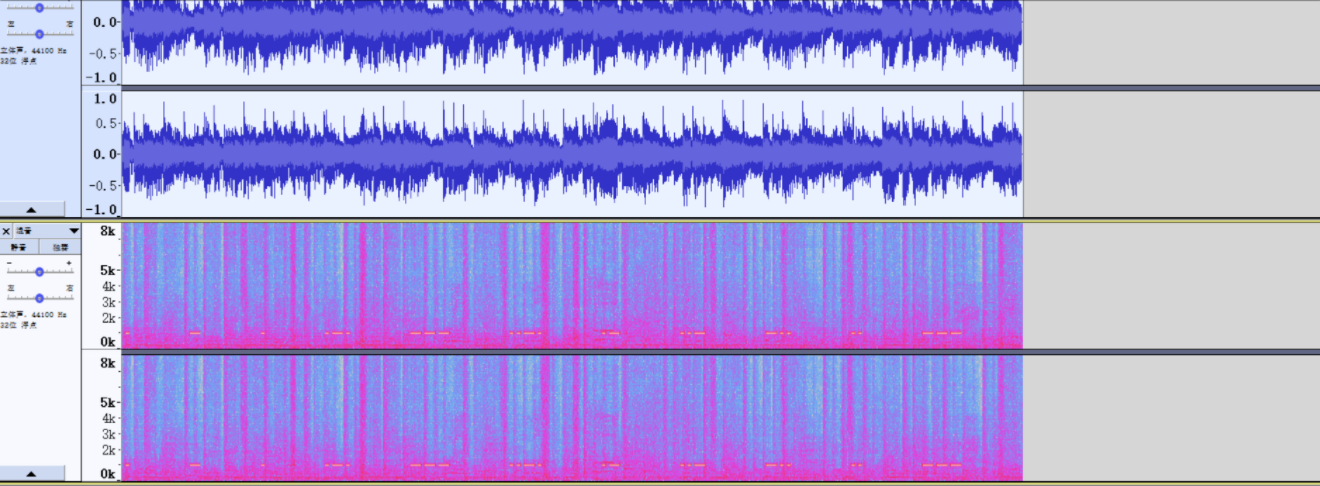
读出摩斯密码!
misound
频谱图中有AnEWmuLTiPLyis_etimes_wiLLbEcomE_B,本以为是前一段flag,没想到是提示。
然后silenteye搞出来base64,翻出来是207 359 220 224 352 315 359 374 290 310 277 507 391 513 423 392 508 383 440 322 420 427 503 460 295 318 245 302 407 414 410 130 369 317
但这个最牛逼的是听起来像个摩斯密码,用sstv分析


用该网站https://www.dcode.fr/dotsies-writing解出来
我们用第一组数乘第二组数,然后除以26就基本确定flag长度了,26这个值可以试出来
或者我们观察第一组乘第二组除以第三组就是26的近似值!