ciscnctf2022
好久没有写博客了,由于期末原因,国赛的逆向还没复现,今天复现一下,总的来说,国赛的三道题,其中两道都是语文题,蚌埠住了。
baby_tree
记得找了很多工具发现并不能转换,所以只能硬看swift的ast代码
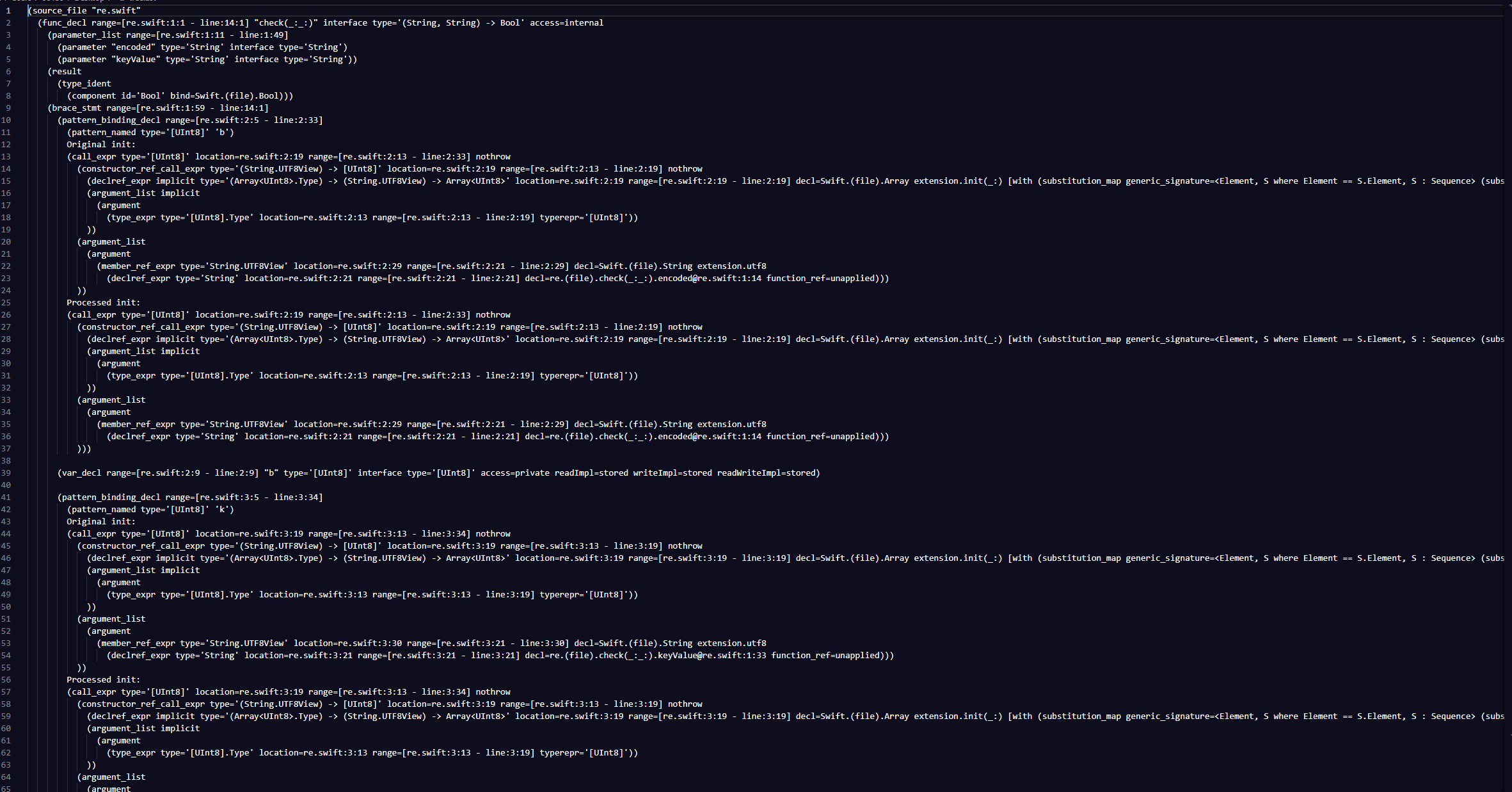
首先我们能发现对比字符串和key的位置
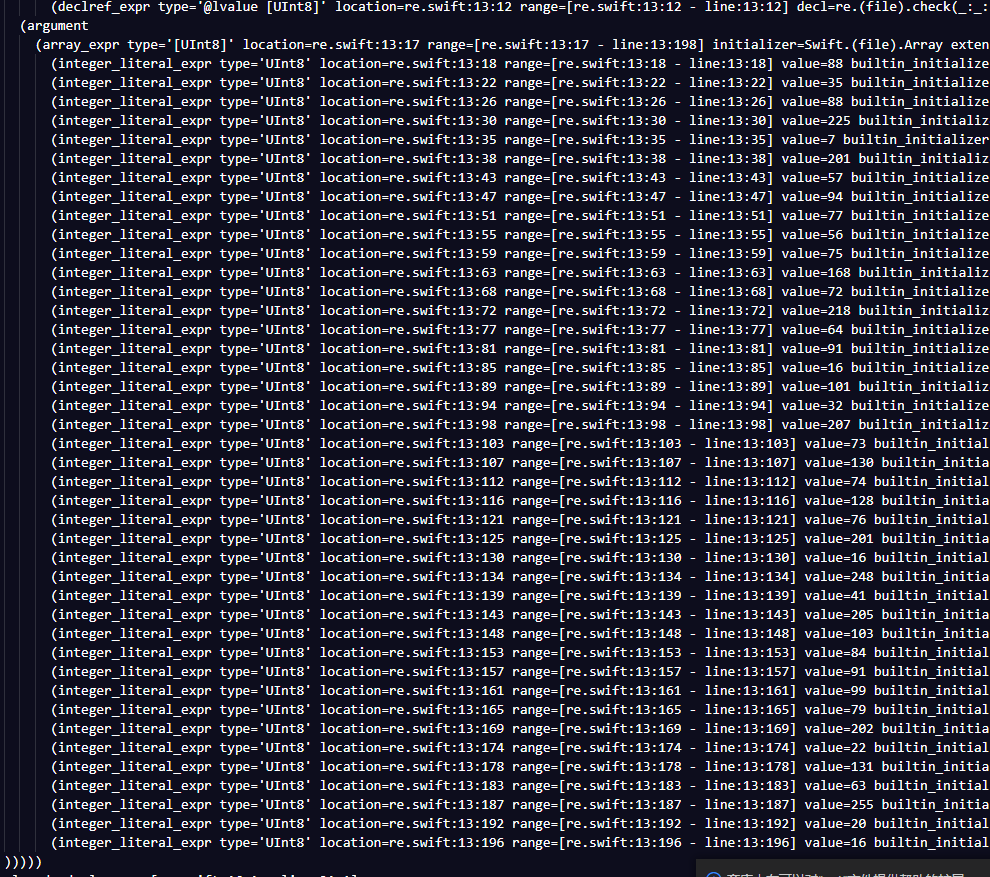
继续往下看在625行大概是调用了check函数,其中传入了两个参数,分别是data和key
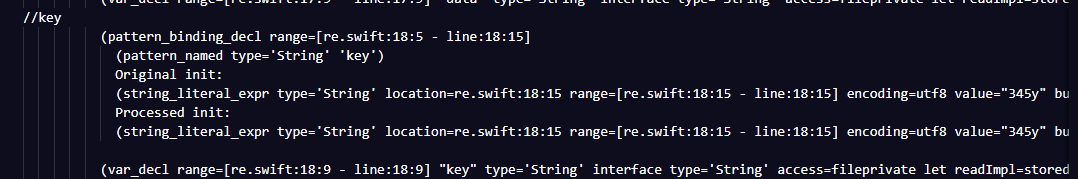
Original init:这个应该是初始化一下,Processed init:这个是运行函数。接下来我们直接查check函数,发现是在最初。
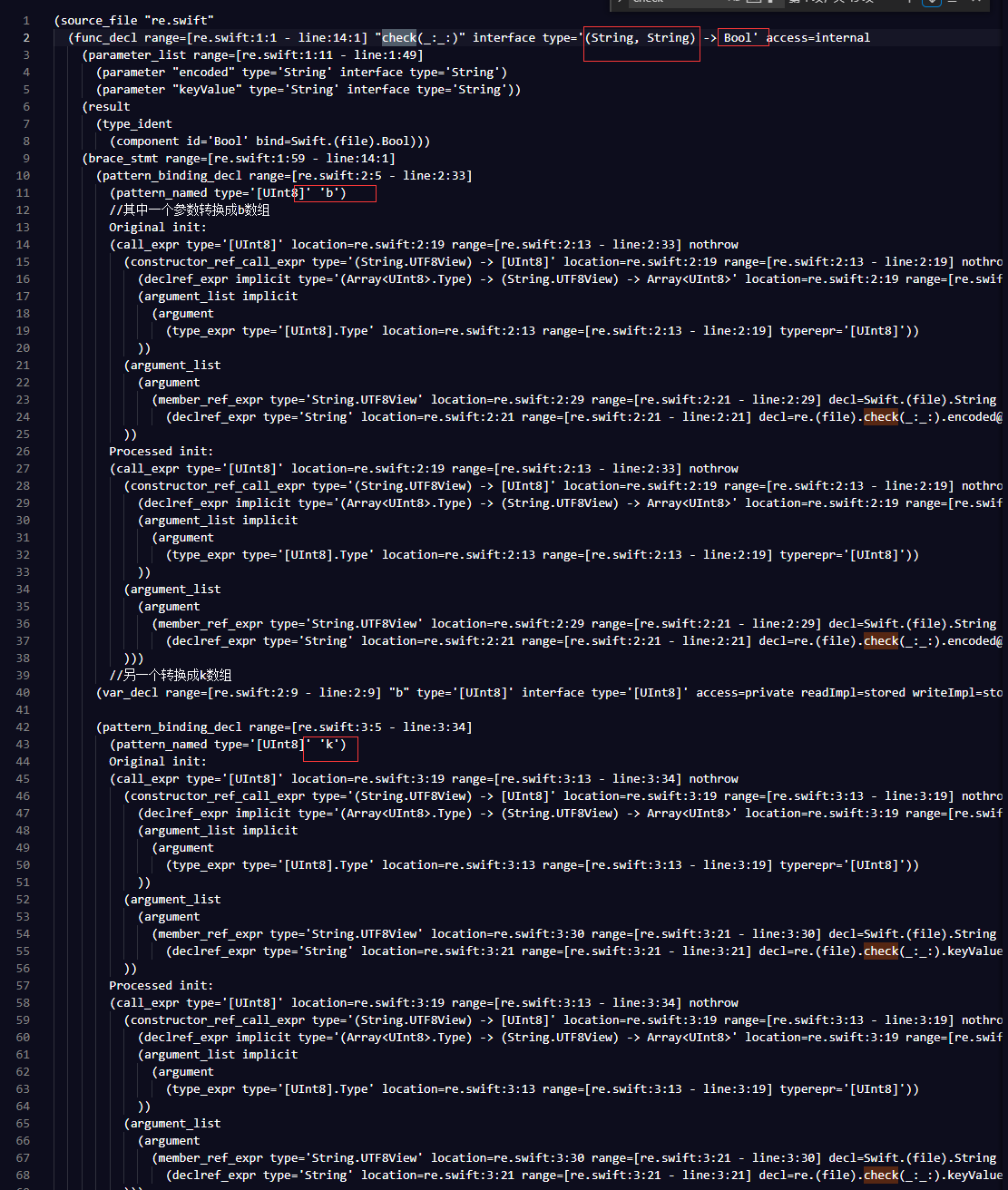
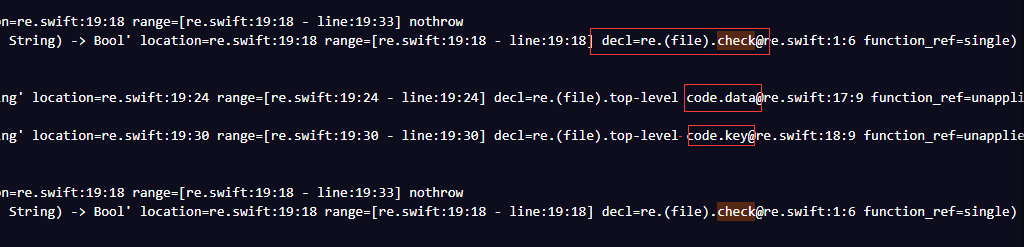
这个地方可以研究一下,其实是传入两个参数,string类型的,这个函数应该是bool类型,这么长的一段并无什么运算符,但可能是将两个string类型转换成数组,一个是b数组,一个是k数组,其中b数组应该是encode的位置,k数组应该就是key。接下来在70行又声明了4个变量r0,r1,r2,r3。继续看在第99行进入循环。
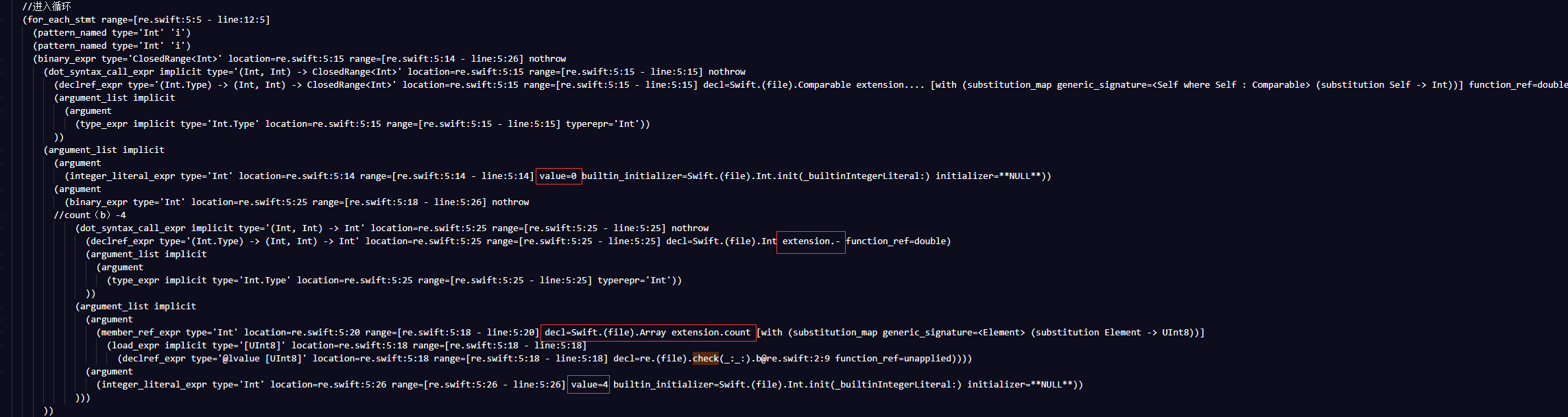
这个循环长度不难猜出是0-cout(b)-4,但如果没看到的话,估计后面几位会错。接下来是个赋值条件,形成第一个元组(r0,r1,r2,r3)
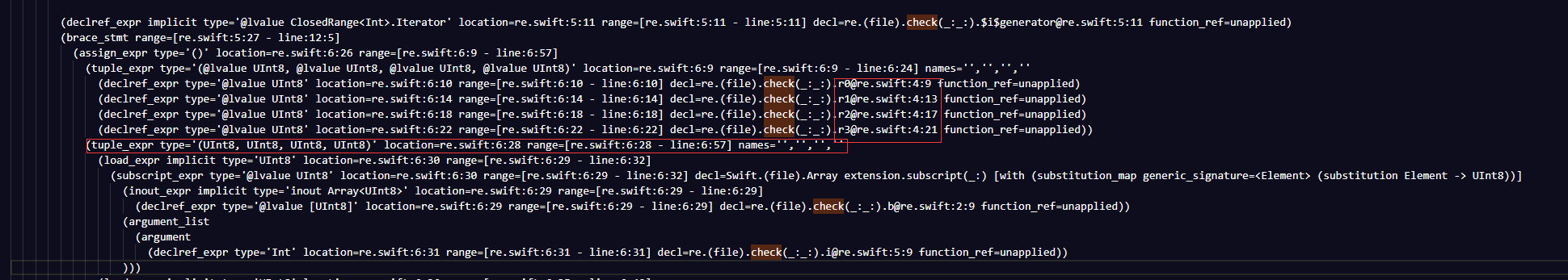
assign_expr和load_expr都是赋值的意思下面通过value的值变换可以猜测,r0,r1,r2,r3 = b[0],b[1],b[2],b[3]
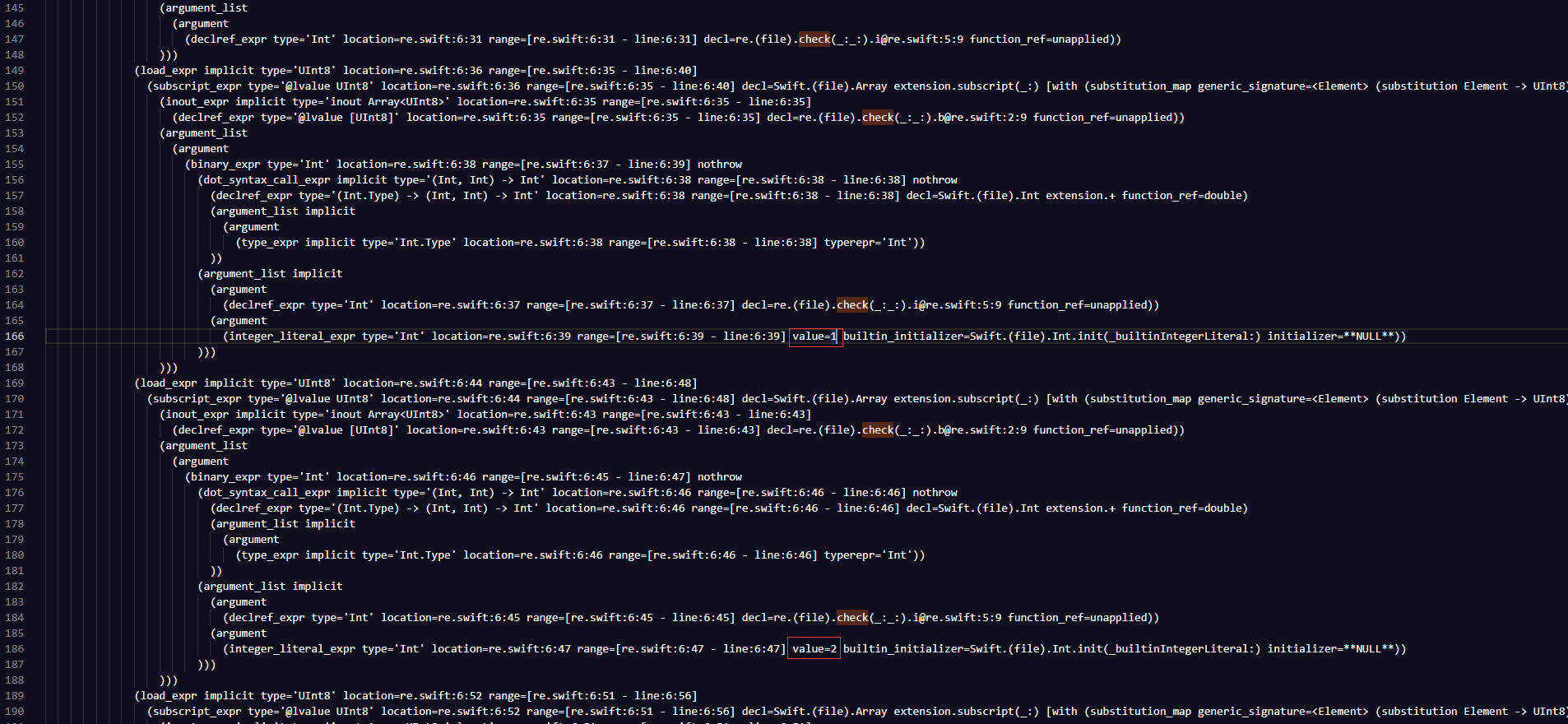
我们分析一个加密:
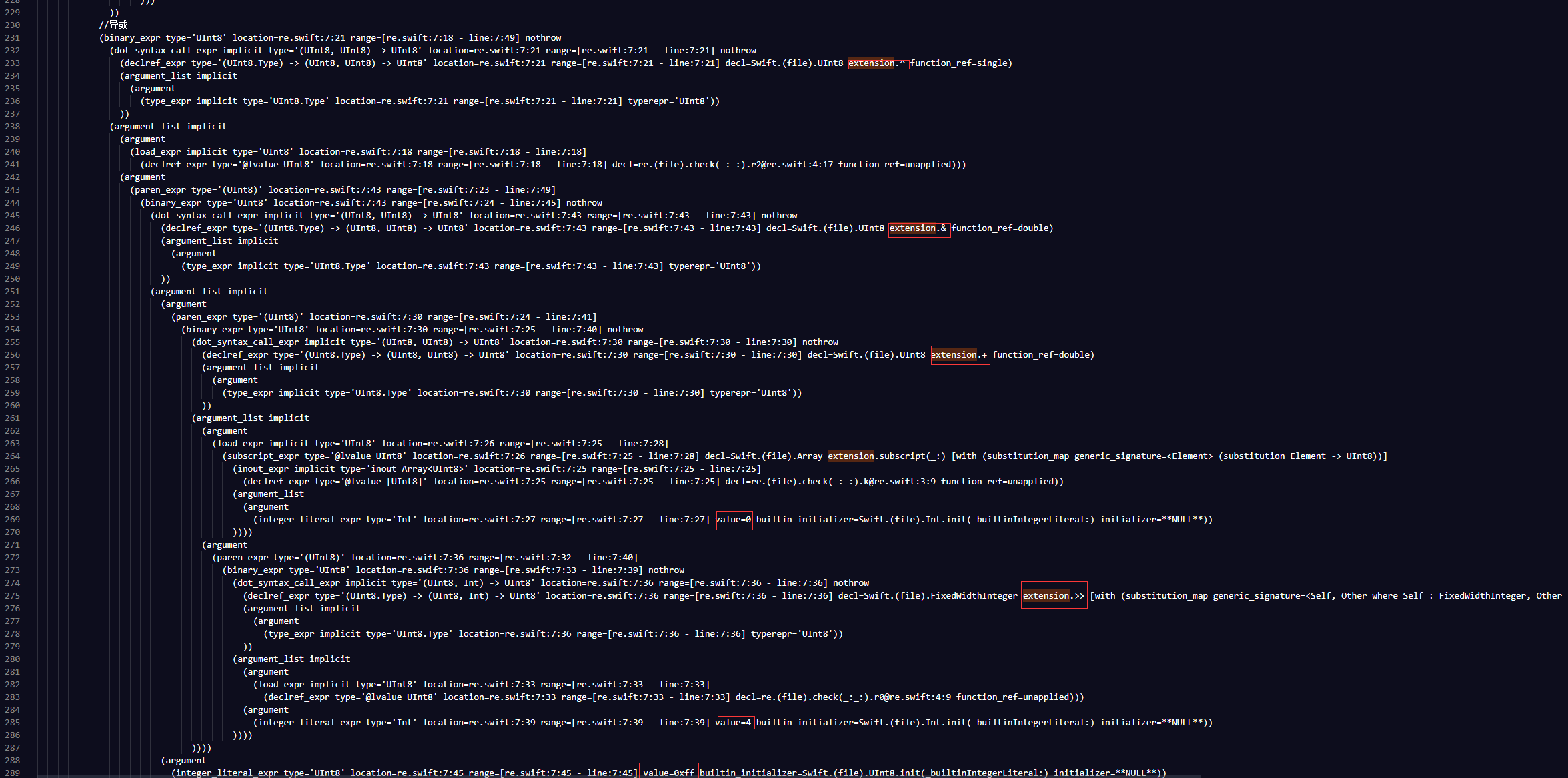
可以看出,缩进代表运算顺序,缩进越多优先级越高,argument后是参数,extension.后是运算符,那么上述图片可以表示为:
1 | b[i+0] = r2 ^ ((k[0] + (r0 >> 4)) & 0xff) |
那么接下来的跟上述是一样的可分析出大概逻辑:
1 | for i in range(0,len(b)-3): |
我们直接写出解密脚本
1 | flag = "" |
本以为这个题就是阅读题的极限了,没想到下一题也是阅读题。
babycode
这个题给了一个.mrb文件后缀是将 ruby 代码编译为 mruby 字节码作为字符串并评估字符串化字节码,通过010前面字符RITE0300,可以判断出mruby的版本是3.1.0,我们下载https://github.com/mruby/mruby/releases/tag/3.1.0源码,首先要安装sudo apt-get install rake,接下来make,然后进入bin里就可以使用mruby了./mruby -v -b babycode.mrb.
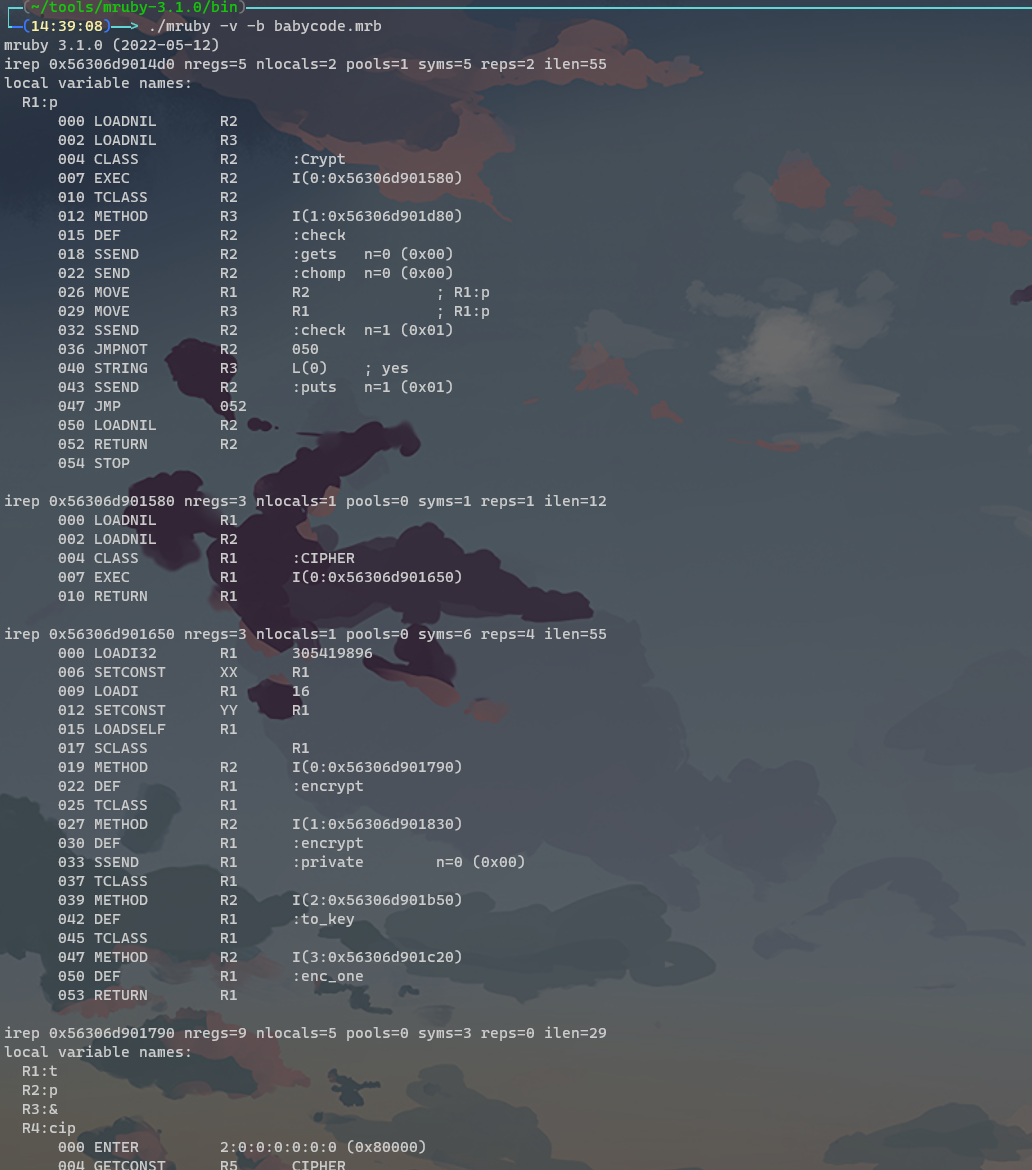
1 | mruby 3.1.0 (2022-05-12) |
经典阅读文档,那天做题的时候大概就已经猜出来是xtea加密,但是应该是还是有别的加密。当然这次再对照着opcode看,在xtea加密前还有一个异或。
1 |
|
1 | a = bytes.fromhex('67080e02194b500d5c585f0b5e40461511470a08154211560d47491e04031d262771217626242765') |
secreeeeet
这类题在外国的ctf见过一次,就是通过加密算法生成图片文件,我们要做的就是解密png文件。代码很多但多数无用,找到主要代码就行
我们通过自己构造flag.png尝试加密,发现每次加密都不一样,可能跟随机数有关
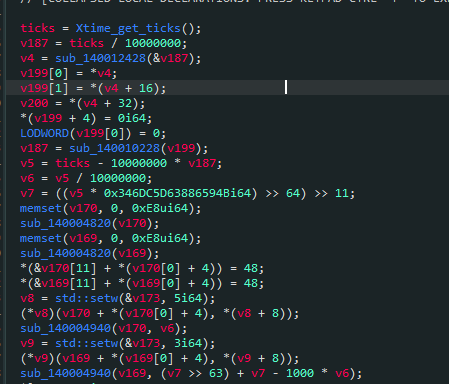
发现在main函数开头调用了Xtime_get_ticks获取时间戳,动态调试发现sub_140004940函数将时间戳从数字变为字符串
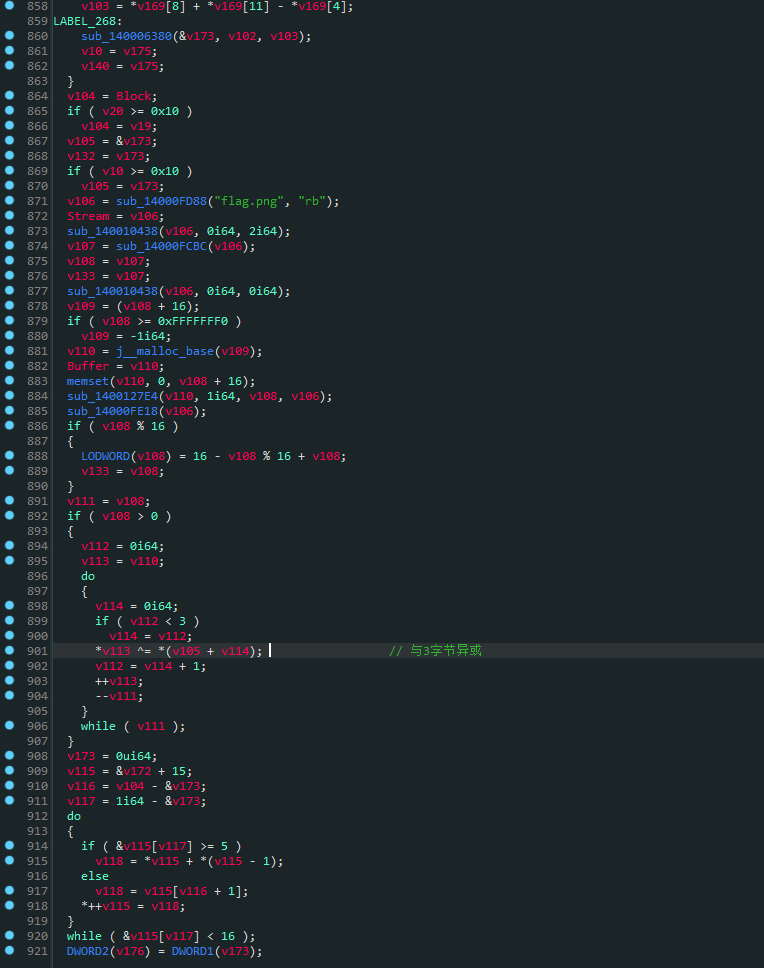
找到主要加密处;这个地方有点逆天,不知道是啥东西,经查阅应该是rabbit流加密
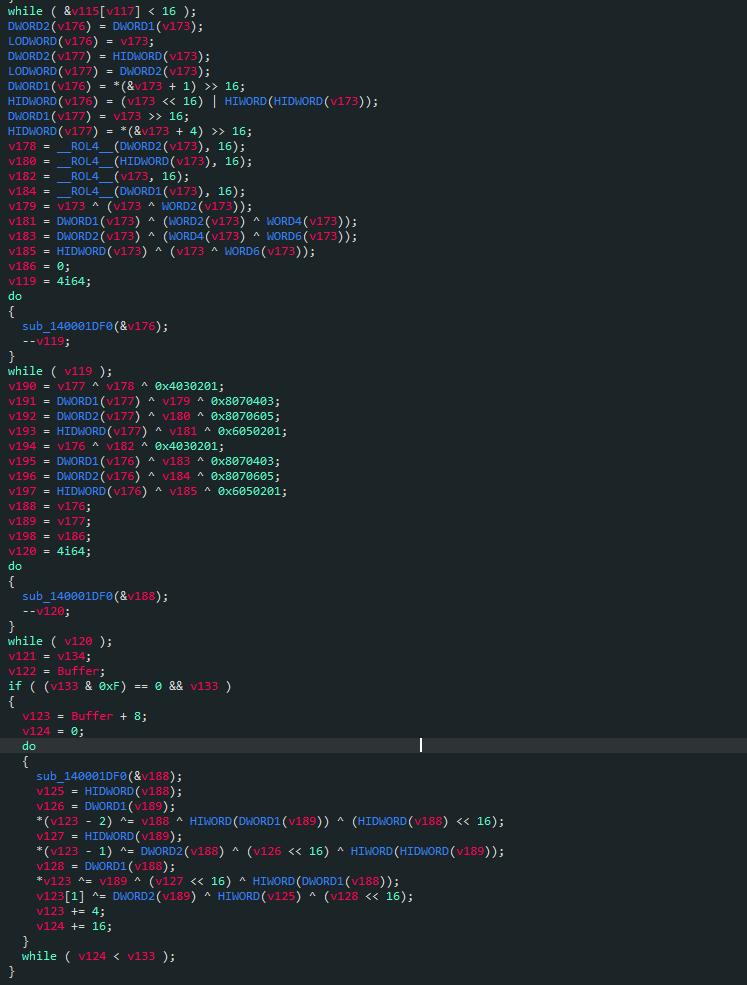
借用REtard师傅的脚本
1 | import struct |
py3版本的rabbit
1 | from rabbit_cipher import Rabbit |
只需要爆破两个key然后逆向rabbit即可